At the core of every enterprise is data, which if lost or exposed might cause irreparable damage to the business or organization. In many instances, regulatory requirements are designed to safeguard data with high penalties if the requirements are not met or if sensitive data is exposed.
Because of this issue, enterprises are experiencing increased pressure from internal and external sources to protect and govern data. These demands are changing the perspective around securely handling data.
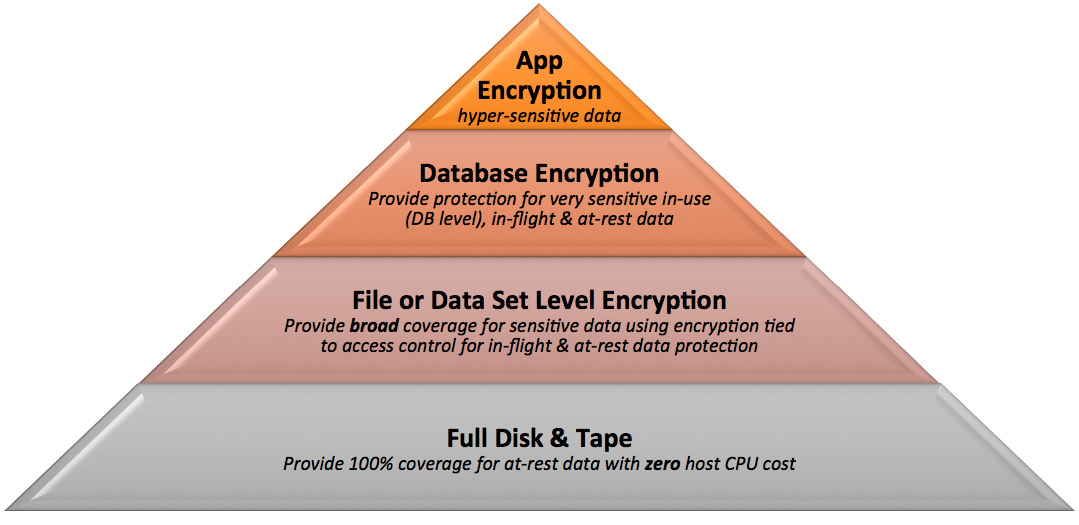
One of the most impactful ways to protect data is to establish a fortified perimeter around that data by using encryption. Protecting the data that is required to achieve compliance should be viewed as a minimum threshold. Best practices suggest a shift from selective encryption (protecting only specific types of data) to pervasive encryption (encrypting all data).
Pervasive encryption for IBM Z platforms is a consumable approach to enable extensive encryption of data in-flight and data at-rest. This approach substantially simplifies encryption and reduces the cost that is associated with protecting data and meeting compliance mandates.
Vicom Infinity is certified and skilled in Pervasive Encryption with IBM Z. We have installed and supported it in organizations, both large and small, and across various industries. We look forward to working with you.